Cisco Security analyzed Snort telemetry coming from Cisco Secure Firewalls to identify the most frequently encountered rules through the lens of the MITRE ATT&CK framework.
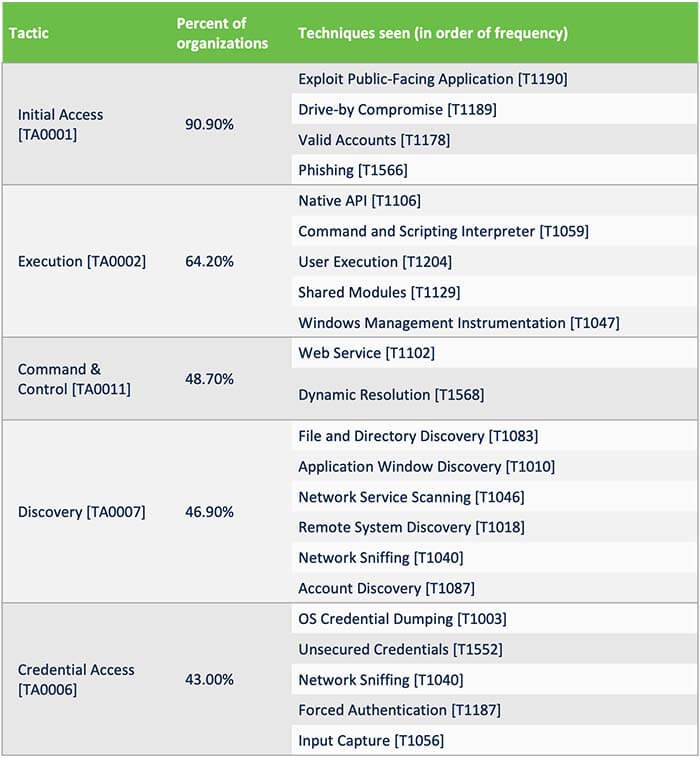
The MITRE ATT&CK framework describes attacker behavior as tactics and includes the actions attackers take to accomplish that behavior as techniques. Many common firewall rules can be mapped to MITRE ATT&CK; the above chart lists the tactics and associated techniques firewalls frequently encounter.
By far, a firewall is more likely to see more Initial Access attempts, which makes sense given its position on the network perimeter. As the above chart shows, 90.9% of organizations saw firewall alerts that fell under this tactic. Within this group, organizations saw exploit attempts against public-facing applications, such as Apache Struts, Bash, and Exchange Servers. Another frequently detected technique associated with Initial Access was the Drive-by Compromise technique, which includes attempts to connect to spoofed websites and access to SMB shares.
Execution attempts were the second most frequent on this list, detected by 64.2% of organizations. Common rules that triggered this type of alert included vulnerabilities in content management systems (CMS), the Zeroshell Linux vulnerability, and an Apache Struts code execution vulnerability.
Apache Struts also featured prominently under Privilege Escalation and Defensive Evasion, two MITRE ATT&CK tactics that didn't make the top five.
Command and Control activity was the third most frequently encountered tactic, with 48.7% of organizations that saw traffic of this type. Much of this traffic consists of suspicious DNS queries, which point to known or likely command-and-control systems.
The Discovery tactic includes techniques such as attempting to traverse administration files in a CMS as well as DNS BIND information disclosure attempts. The Discovery tactic was fourth most frequently detected.
The Credential Access tactic rounds out the top five. Techniques include credential dumping attacks, such as those targeting routers and IoT devices such as CCTV cameras. Organizations also saw firewall alerts for attempts to exploit vulnerabilities that could provide administrator credentials or attempts to access PHP configuration files.
Read more about firewall threat trends on the Cisco Secure blog.
"tactic" - Google News
November 04, 2021 at 04:09AM
https://ift.tt/3wr6sFj
5 MITRE ATT&CK Tactics Most Frequently Detected by Cisco Secure Firewalls - Dark Reading
"tactic" - Google News
https://ift.tt/2NLbO9d
Shoes Man Tutorial
Pos News Update
Meme Update
Korean Entertainment News
Japan News Update
Bagikan Berita Ini














0 Response to "5 MITRE ATT&CK Tactics Most Frequently Detected by Cisco Secure Firewalls - Dark Reading"
Post a Comment